Zcash: Privacy Pioneer Built on Zero-Knowledge Proofs

Zcash enables private cryptocurrency transactions through zk-SNARKs technology. Complete analysis of features, adoption, and future prospects.
Crypto Rich
November 19, 2025
Table of Contents
Zcash is a decentralized cryptocurrency that enables completely private transactions while maintaining network security through zero-knowledge cryptography. Where most blockchains expose all transaction details publicly, Zcash gives users a choice: visible payments or fully encrypted transfers through its dual-address system of transparent t-addresses and shielded z-addresses.
Launched in 2016 as a Bitcoin fork, the project introduced zk-SNARKs (Zero-Knowledge Succinct Non-Interactive Arguments of Knowledge) to the cryptocurrency space. This innovation positioned Zcash as the flagship project for financial privacy in crypto, pioneering techniques that have since influenced major blockchains, including Ethereum's scaling solutions.
Why Financial Privacy Matters in Cryptocurrency
Blockchain transparency creates a permanent public record of every transaction. While this enables verification and audit, it also exposes sensitive financial information that wouldn't be visible in traditional banking. Every purchase, every payment, every wallet balance becomes public knowledge.
For individuals, this means anyone can track spending patterns, estimate wealth, and identify transaction counterparties. For businesses, transparent blockchains expose supplier relationships, pricing strategies, and financial positions to competitors. Zcash addresses these privacy concerns while maintaining the security and decentralization that make cryptocurrency valuable.
How Did Zcash Originate and Evolve?
Zcash emerged from years of academic research into zero-knowledge proofs at institutions including Johns Hopkins University and the Technion. The project forked from Bitcoin, inheriting its proof-of-work model and 21-million-coin supply cap. The bold innovation? Integrating zk-SNARKs directly into the protocol layer.
October 28, 2016 marked the mining of the first block and the debut of privacy-preserving peer-to-peer payments at the protocol level. The Zcash Company, later rebranded as the Electric Coin Company (ECC), spearheaded early development alongside an expanding research community that included some of the world's leading cryptographers.
Major Protocol Upgrades Shape Network Evolution
Sapling arrived in 2018 as a watershed moment. Before this upgrade, generating a shielded transaction required several minutes of computation and over 3GB of memory. Mobile wallet usage? Impractical.
Sapling slashed proof generation time to just seconds and memory requirements to under 40MB through new elliptic curves (BLS12-381) optimized for pairing-based cryptography.
Heartwood followed in 2020, enhancing scalability and miner flexibility. The upgrade enabled more efficient block propagation and introduced Flyclient support, letting light clients sync with the blockchain by sampling block headers rather than downloading the entire chain.
Network Upgrade 5 Eliminates Trusted Setups
Network Upgrade 5 (NU5) in 2022 brought transformative changes that addressed long-standing concerns. The upgrade delivered three critical advances:
- Halo 2 proof system eliminated the need for trusted setup ceremonies that previously required elaborate multi-party computation to generate cryptographic parameters
- Unified addresses combined transparent and shielded address functionality into a single format, letting wallets automatically select the appropriate transaction type
- Enhanced proof efficiency improved both generation and verification speed, reducing computational burden for users and nodes
Governance has shifted toward greater community participation over time. What began as a largely founder-driven project evolved into a more decentralized ecosystem where community votes determine funding allocations and protocol direction.
What Technology Powers Zcash's Privacy Features?
Zcash operates on a proof-of-work blockchain using the Equihash algorithm, explicitly chosen for its resistance to ASIC-dominated mining and emphasis on memory-hard computation. While ASIC miners eventually emerged, the algorithm's design still provides more mining decentralization than Bitcoin's SHA-256.
The network maintains Bitcoin's fundamental monetary characteristics with four-year halving cycles. This familiar economic model provides predictable issuance that mirrors Bitcoin's scarcity properties while adding what Bitcoin lacks: privacy features.
Transparent vs. Shielded Addresses
Transparent addresses (t-addresses) work identically to Bitcoin addresses. All transaction details display publicly on-chain. Anyone can view the sender, receiver, and amount.
Shielded addresses (z-addresses) change the game. They encrypt transaction information using zk-SNARK technology, hiding amounts and participants while still letting the network verify transaction validity.
This represents a fundamental departure from transparent blockchain design, creating a system where cryptography enforces privacy.
How zk-SNARKs Work
zk-SNARKs are sophisticated cryptographic proofs that confirm transaction correctness without exposing underlying data. When someone sends a shielded transaction, they generate a proof.
That proof demonstrates they possess sufficient funds, that no coins are created or destroyed, and that the transaction follows all protocol rules. The network verifies the proof's validity without learning anything about the transaction's actual details.
The capabilities are remarkable. Miners and nodes confirm legitimacy without knowing who sent it, who received it, or how much was transferred.
The shielded pool acts as a cryptographic mixing service where transactions blend together, strengthening privacy for everyone as adoption grows.
The mathematics underlying zk-SNARKs involve elliptic curve cryptography and polynomial commitments. These create proofs that are "succinct" (small in size) and "non-interactive" (requiring no back-and-forth communication).
These properties make zk-SNARKs practical for blockchain implementation, where proof size and verification speed directly impact network scalability.
Current development focuses on post-quantum cryptographic resistance, preparing for future computational threats. Quantum computers capable of breaking current elliptic curve cryptography remain years or decades away. But proactive development ensures Zcash will remain secure as computational capabilities evolve.
How Does Zcash's Governance Structure Work?
Development proceeds through the Zcash Improvement Proposal (ZIP) process, an open governance framework where community members propose, debate, and refine protocol changes. This transparent approach ensures thorough vetting before implementation.
Anyone can submit a ZIP. The proposal must follow a standardized format that describes its motivation, technical specifications, security considerations, and implementation details.
Draft ZIPs receive community feedback, undergo revision, and eventually move toward acceptance or rejection based on technical merit and community consensus.
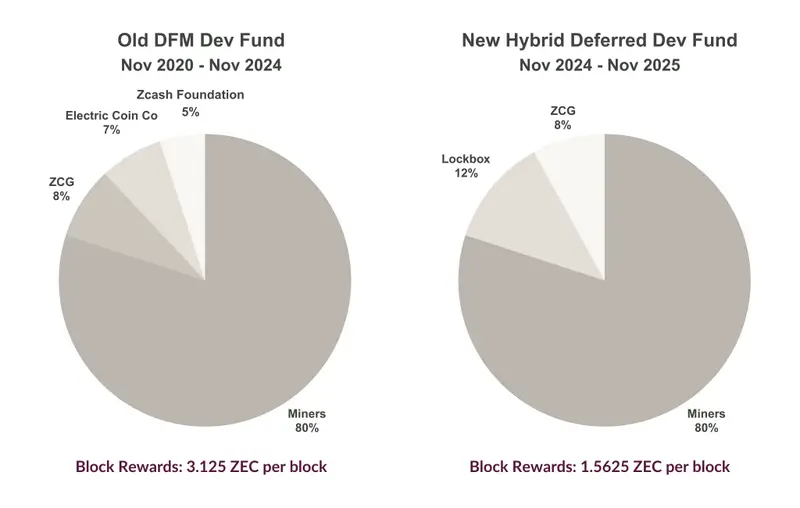
Development Fund Allocation
Funding comes from a development fund carved from block rewards. As of November 2024, the allocation structure changed significantly from the previous model.
Currently, 80 percent of block rewards go to miners securing the network. The remaining 20 percent supports ongoing development and ecosystem growth through:
- Zcash Community Grants Committee (ZCG) receives 8 percent to fund independent teams and projects in the Zcash ecosystem
- Lockbox fund receives 12 percent, held in reserve until the community decides on a suitable decentralized mechanism for future distribution
This structure creates sustainable long-term funding without relying on external corporate sponsors or venture capital. Unlike projects that conduct large initial coin offerings or receive substantial VC backing, Zcash's development funding comes directly from block rewards. This aligns developer incentives with network success over time.
The previous funding model (November 2020 - November 2024) allocated resources to the Electric Coin Company, Zcash Foundation, and ZCG. The new model reflects the community's evolution toward more decentralized governance, with ZCG handling ecosystem development while the lockbox mechanism awaits community consensus on optimal distribution methods.
Community votes determine allocation adjustments, maintaining decentralized control over project direction. The Zcash Community Advisory Panel provides input on development priorities and funding decisions, ensuring stakeholder voices influence protocol evolution.
Where Is Zcash Being Used Today?
Zcash's combination of optional privacy and technical reliability creates practical applications across multiple sectors. The shielded pool enables genuinely private peer-to-peer payments without exposing transaction history to surveillance.
Real-World Privacy Applications
Individuals and organizations use Zcash for private savings and value storage. They benefit from both the privacy features and the predictable monetary policy.
Where transparent blockchains let anyone view wallet balances and transaction history, Zcash shielded addresses keep holdings completely private while still providing cryptographic proof of legitimate ownership.
Privacy-focused services increasingly integrate Zcash for subscription payments. The partnership with NymVPN demonstrates how privacy-preserving cryptocurrencies align with privacy-protecting services. Users paying for VPN access with shielded ZEC maintain complete financial privacy throughout the transaction chain.
Cross-chain interoperability layers like Router Protocol enable shielded assets to move between different blockchain ecosystems. Users can enter and exit various decentralized finance protocols while maintaining transaction confidentiality.
This addresses a critical gap in DeFi where transparent transactions expose trading strategies and holdings.
Merchants accepting cryptocurrency payments increasingly recognize Zcash as a viable option, particularly for customers prioritizing financial privacy. Transparent cryptocurrencies expose customer purchase history. Zcash shielded transactions protect customer privacy while still providing merchants with payment certainty and low fees.
Wallet Development Drives Adoption
The Zashi wallet represents a significant step toward mainstream adoption. It defaults to shielded transactions rather than treating privacy as an advanced feature.
This design philosophy acknowledges a simple truth: most users accept default settings without understanding technical implications. Privacy-by-default becomes crucial for widespread adoption.
The wallet's interface simplifies the distinction between transaction types. It automatically selects the appropriate option based on recipient capabilities and user preferences. This abstraction hides complexity that previously deterred non-technical users.
Major exchanges continue to support ZEC trading despite regulatory pressures on privacy-focused cryptocurrencies. Platforms including Coinbase, Kraken, Gemini, and numerous others provide ZEC trading pairs. Global users can acquire and trade Zcash through established platforms.
This accessibility proves crucial for mainstream adoption. Most cryptocurrency users prefer the convenience of centralized exchanges. The continued support demonstrates that Zcash's optional privacy model strikes a balance satisfying both user privacy needs and regulatory requirements in many jurisdictions.
What Challenges Does Zcash Face?
Regulatory scrutiny represents the most significant ongoing challenge for Zcash and other privacy-focused cryptocurrencies. Government agencies in multiple jurisdictions view optional privacy features with suspicion, associating them with money laundering and sanctions evasion.
The reality? Legitimate privacy use cases far outnumber criminal applications.
Regional Restrictions and Market Fragmentation
This perception has led to exchange delistings in certain regions. South Korea banned privacy coin trading on domestic exchanges in 2021. Japan required exchanges to delist privacy-focused cryptocurrencies.
Parts of Europe have seen exchanges proactively remove privacy coins to avoid potential regulatory complications. The result is a fragmented global market where Zcash availability varies significantly by region.
The technical complexity of zk-SNARKs creates barriers for developers and users alike. Generating shielded transaction proofs requires more computational power than transparent transactions, impacting mobile wallet performance.
This complexity also makes security audits more challenging. Fewer experts possess the specialized cryptographic knowledge needed for a comprehensive review of zero-knowledge proof systems.
Competition and Market Perception
Monero is the primary competitive alternative due to its mandatory privacy model. All transactions are encrypted by default. Unlike Zcash's optional approach, Monero provides no transparent transaction option.
Monero advocates argue that optional privacy weakens the anonymity set. Users choosing transparent transactions don't contribute to the shielded pool's privacy properties.
Zcash supporters counter that optional privacy provides flexibility for regulatory compliance and for use cases that require transparency for auditing purposes.
Public perception remains mixed. Legitimate privacy advocates compete with associations linked to illicit activity. Privacy is a fundamental right in financial transactions, yet media coverage often emphasizes darknet market use rather than lawful applications such as protecting business confidentiality or avoiding financial surveillance.
What Recent Developments Are Shaping Zcash?
Network Upgrade 6.1 (NU6.1) (November 23, 2025) focuses on shielded transaction accuracy improvements and enhanced reliability for edge cases discovered through production usage. These incremental refinements demonstrate Zcash's commitment to production-grade stability.
Technical Infrastructure Improvements
The transition to Rust-based node implementations marks a significant shift in technical foundation. Rust's memory safety properties prevent a wide range of security vulnerabilities that plague C and C++ implementations.
Buffer overflows, memory management issues, and other vulnerabilities that have caused critical problems in cryptocurrency software simply can't happen in properly written Rust code.
This migration also aligns Zcash with broader trends in the cryptocurrency industry. Projects such as Polkadot, Solana, and others recognize Rust's advantages for security-critical systems. The shared ecosystem creates opportunities for code reuse and collaboration while attracting Rust developers to contribute to Zcash development.
Deeper integration with zero-knowledge ecosystems continues expanding Zcash's relevance beyond its core privacy use case. The protocol's pioneering work with zk-SNARKs established foundational knowledge that now powers Ethereum's rollup scaling solutions, zkSync, StarkWare, and various layer-two protocols.
Cross-Chain Privacy Development
Interoperability projects increasingly recognize privacy as a missing component in cross-chain infrastructure. Bridges and wrapped assets enable value transfer between blockchains, but they typically inherit the transparency of their destination chains. Transaction details get exposed.
Integrating Zcash's shielded pool into cross-chain workflows offers a privacy-preserving alternative. Router Protocol and similar interoperability layers work toward enabling shielded cross-chain transactions that preserve privacy throughout the transfer process.
These developments reflect growing recognition that financial privacy remains essential even as blockchain technology becomes mainstream. Corporate treasuries holding cryptocurrency face particular challenges from blockchain transparency.
Public transaction records expose trading strategies and financial positions to competitors. Privacy-preserving alternatives become increasingly attractive as more organizations recognize these information disclosure problems.
Can Zcash Remain Relevant as Competition Intensifies?
Zcash's position as the first major cryptocurrency implementing zero-knowledge proofs provides lasting advantages despite newer competitors. The network's operational history since 2016 demonstrates reliability that newer projects cannot claim. This builds trust among users who prioritize proven infrastructure.
The project's academic foundations continue generating research contributions that benefit the entire cryptocurrency ecosystem. Universities and research institutions studying zero-knowledge cryptography frequently reference Zcash's implementation. They use it as a case study to generate insights that advance the field.
Unlike many competitors that rely on venture capital funding or token distributions that concentrate ownership, Zcash's development funding from block rewards creates more sustainable, long-term incentives. This model avoids the pressure for premature scaling that plagues VC-backed projects needing quick returns.
The absence of a large initial coin offering means Zcash avoided the wealth concentration that characterizes many cryptocurrency projects.
What Comes Next for Zcash Development?
The roadmap emphasizes expanding decentralized finance integrations while maintaining core privacy features. Bringing shielded assets into lending protocols, decentralized exchanges, and other DeFi primitives requires solving complex technical challenges around private smart contract execution.
Future Technical Priorities
Research into zero-knowledge virtual machines explores creating execution environments where smart contracts can operate on encrypted state. The goal? Maintaining privacy while providing the programmability that makes DeFi applications possible.
This represents a significant technical challenge requiring new cryptographic techniques.
Cross-chain privacy remains a major focus area as blockchain interoperability becomes increasingly important. Key development areas include:
- Threshold signatures and multi-party computation allowing distributed validators to manage wrapped assets without any single party learning transaction details
- Privacy-preserving bridges enabling assets to move between chains while maintaining confidentiality throughout the transfer process
- Mobile wallet optimization reducing computational requirements for shielded transactions to improve user experience on resource-constrained devices
The balance between privacy, performance, and decentralization creates ongoing challenges requiring careful engineering tradeoffs. Stronger privacy often requires more complex cryptography that increases computational requirements. Better performance sometimes involves centralization that undermines censorship resistance.
Conclusion
Zcash pioneered privacy-preserving cryptocurrency through zero-knowledge proofs, creating a system in which users control their financial privacy. The dual-address approach balances transparency with privacy across different regulatory environments and use cases.
Nearly a decade of technical achievements demonstrates commitment to production-grade reliability. As digital surveillance expands and financial privacy becomes scarcer, Zcash's influence extends beyond its own network through research contributions shaping the entire zero-knowledge ecosystem.
Visit the official Zcash website for more information and follow @zcash on X for the latest updates.
Sources:
- Electric Coin Company - Zcash Development Updates and Technical Documentation
- Zcash Foundation - Governance and Community Resources
- Zcash Improvement Proposals - Protocol Specifications
- Zcash Protocol Specification - Technical Documentation
- CoinMarketCap - Coin information
Read Next...
Frequently Asked Questions
What makes Zcash different from Bitcoin?
Zcash builds on Bitcoin's foundation but adds optional privacy through zk-SNARK technology. Users can choose transparent transactions like Bitcoin or shielded transactions that encrypt sender, receiver, and amount while remaining fully verifiable on-chain. Both share proof-of-work consensus and a 21-million coin supply cap.
How secure are Zcash's shielded transactions?
Shielded transactions use zero-knowledge cryptography that has undergone extensive academic review and security audits since 2016. The protocol has operated without major security breaches, and recent upgrades eliminated trusted setup requirements that previously represented theoretical vulnerabilities. Multiple independent security audits verify the cryptographic soundness of the proof systems.
Why do some exchanges not support Zcash?
Regulatory concerns about privacy features lead some exchanges to avoid listing privacy-focused cryptocurrencies in jurisdictions with strict anti-money-laundering enforcement. However, many major exchanges including Coinbase, Kraken, and Gemini continue supporting ZEC trading, providing access for users in regions where privacy coins remain legal.
Can law enforcement trace Zcash transactions?
Shielded transactions encrypt all details and cannot be traced through blockchain analysis. However, users can optionally share viewing keys that reveal specific transaction details to chosen parties, enabling compliance with legal requirements when necessary.
What is the difference between Zcash and Monero?
Monero requires all transactions to be private by default, while Zcash offers optional privacy through its dual-address system. This makes Zcash more flexible for users needing transparent transactions for compliance or audit purposes while providing strong privacy when desired. Both approaches have tradeoffs between privacy guarantees and flexibility.
Disclaimer
Disclaimer: The views expressed in this article do not necessarily represent the views of BSCN. The information provided in this article is for educational and entertainment purposes only and should not be construed as investment advice, or advice of any kind. BSCN assumes no responsibility for any investment decisions made based on the information provided in this article. If you believe that the article should be amended, please reach out to the BSCN team by emailing [email protected].
Author
 Crypto Rich
Crypto RichRich has been researching cryptocurrency and blockchain technology for eight years and has served as a senior analyst at BSCN since its founding in 2020. He focuses on fundamental analysis of early-stage crypto projects and tokens and has published in-depth research reports on over 200 emerging protocols. Rich also writes about broader technology and scientific trends and maintains active involvement in the crypto community through X/Twitter Spaces, and leading industry events.
Crypto Project & Token Reviews
Project & Token Reviews
Comprehensive reviews of crypto's most interesting projects and assets
Learn about the hottest projects & tokens